
We’ve all received the classic email from a foreign investor promising to transfer millions of dollars into our bank account if we just provide a few sensitive details. You probably didn’t fall for that. But these fraudulent attempts to obtain sensitive information – known as phishing scams – are getting more sophisticated. Even here at Sive.Host, we’ve seen a few scammers attempting to replicate our email notifications.
Let’s unpack the purpose of phishing, how to identify potential phishing scams and – most importantly – how to prevent getting scammed.
The purpose of phishing
The goal with phishing scams is simple: to gain access to your personal details. This includes email addresses as well as banking or login details. Phishing scams want to steal your access details because of what those access details unlock. For example, if it’s mailbox details then the purpose may be fraud, sending spam or stealing personal information. Banking details will almost always be used to steal money, while login details for e-commerce sites or credit card details could be used to make fraudulent purchases.
There are a few tell-tale signs of a phishing scam. Once you understand the methods used, you’ll be able to guard against them.
How to identify potential phishing scams
No matter how high-tech the phishing scam, it essentially works like an old-fashioned con job: someone has to convince you that they’re reliable before they try to steal from you.
This is most often done through fake emails that look like they come from a trusted source. The email will ask – with some urgency – for you to click on a link to a spoofed website. The website will be convincingly designed to look legitimate and from a service provider you’re most likely to use, and ask for sensitive user information. Once the information is obtained, it can be used for identity theft, financial theft or fraud.
So how do you identify which emails are legitimate and which are phishing scams?
4 golden rules for identifying phishing scams
- Don’t trust the logo or email address
It’s easy enough for phishers to copy a real company logo, and even fake the “From:” email address to look like it comes from a trusted source. Don’t trust the display name, as those are easily changed to mask the real email address. - Be suspicious of urgent requests
If there’s one thing to take away from this article, it should be this: a trusted company will never ask you to change your password via a link in an email. Phishers can use these links to obscure the actual URL, which takes you to a fake account. Nor would they randomly suspend your account and ask you to log in via a link to fix the situation, or risk your account being closed. A trusted company will give you the full URL in the text, not a link. The safest thing to do is type out the URL in your browser, rather than clicking on it. - Check for typos or spelling mistakes
Reputable companies have copywriters to check their emails, so if you’re noticing bad grammar and typos, be on the alert. Similarly, check the URL of the company for misspellings or strange versions of the URL (www.sivehostZA.com instead of www.sive.host, for example). If in doubt, copy-paste the URL directly into your browser. - Don’t open unexpected attachments
A common phishing tactic is spreading viruses and malware through attachments, which can damage files or steal passwords from your computer. If you get an email containing an unexpected attachment, double check the sender’s email address before clicking on the attachment.
Example of a phishing email impersonating a brand:
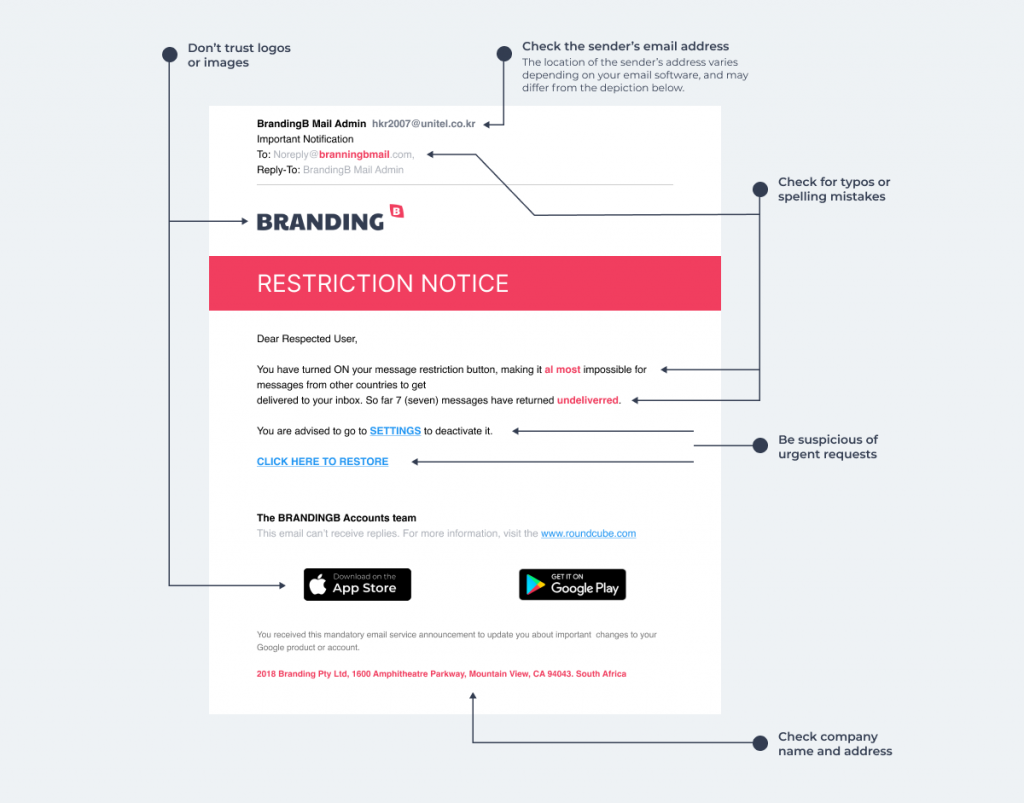
Simple ways to prevent being scammed
The best defence is to identify potential phishing scams, as outlined above. Here are a few additional steps to protect you:
- Check the URL in your browser
Before you log in to any site, check the URL in the address bar. If you know your bank’s URL is www.fnb.co.za, don’t log in to www.bank-fnb.co.za/login.php. Also double-check the URL is spelt correctly: www.sive.hosst is not the same as www.sive.host - Only use a strong password
Using a weak password that you use elsewhere and have used for the past few years is not a good idea. Here are some tips on how to change a mail password. - Delete emails that ask for personal information
Don’t reply, click on links or call phone numbers in these emails. Either delete them or report them as spam. - Never email personal or financial information
Email is not a secure enough method to send personal or financial information – rather call through the information where possible, or split it up over email and text messages. If you’re transferring large sums into someone’s bank account, always verify their banking details telephonically first. A common exploit is for phishers to gain access to your email account and then modify invoices to reflect their own bank account details. - Review credit card and bank account statements
It’s important to check your credit card and bank statements as soon as you receive them to check for suspicious or unauthorised charges. - Don’t share your password on the phone
A reputable company won’t cold call you and ask you to give them your password over the phone. This technique can be successful because people will share details over the phone when they’re in a hurry. Don’t fall for it! - Never click on suspicious links or open attachments
Attachments are an open invitation for Malware and Spyware. Make your your anti-virus protection is up-to-date and run regular scans. - Use two-factor authentication
Add an extra layer of protection to your accounts as a preventative measure. 2FA requires an extra step to verify account details, preventing unauthorised usage.
And finally, notify the company that’s being impersonated so that they can take immediate action.
Phishing scams may seem intimidating, but armed with this knowledge you’ll be able to identify them, and send them straight where they belong: in the trash.


