Nobody likes or wants SPAM. And yet our inboxes are full of it.
It is not only plain intrusive, it also puts our online identity at risk. Phishing attacks have only been on the rise ever since they came into existence.
It’s not easy to detect phishing emails
While some of the emails we receive are obvious spam, most of them are not very easy to recognise just by seeing the content or the sender.
But there’s a way..
Here comes the advance debugging of email which is commonly known as analysing the email headers. Let’s understand what email headers are and how they can help in detecting fraudulent emails.
Generally only the basic information is displayed on the normal email header. Some examples of normal email header in different mail clients:
Gmail
Thunderbird

As you notice, most email readers only show the From: and To: headers, which can be easily forged. The complete message headers will look something like this:
Delivered-To: someguy@gmail.com
Received: by 10.200.41.121 with SMTP id z54csp461727qtz;
Sun, 8 Jan 2017 04:33:03 -0800 (PST)
X-Received: by 10.55.157.17 with SMTP id g17mr82034336qke.122.1483878783846;
Sun, 08 Jan 2017 04:33:03 -0800 (PST)
Return-Path: <0-1111323-gmail.com@delivery.seasonsms.com>
Received: from trans.pepitrans01.com (trans.pepitrans01.com. [103.52.181.228])
by mx.google.com with ESMTPS id 94si44473076qtb.140.2017.01.08.04.33.03
for <someguy@gmail.com>
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Sun, 08 Jan 2017 04:33:03 -0800 (PST)
Received-SPF: pass (google.com: domain of 0-22228-gmail.com@delivery.seasonsms.com designates 103.52.181.228 as permitted sender) client-ip=103.52.181.228;
Authentication-Results: mx.google.com;
dkim=pass header.i=@delivery.seasonsms.com;
header.i=@delivery.seasonsms.com;
spf=pass (google.com: domain of 0-22228-gmail.com@delivery.seasonsms.com designates 103.52.181.228 as permitted sender) smtp.mailfrom=0-22228-gmail.com@delivery.seasonsms.com
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=pepipost; d=delivery.seasonsms.com;h=Message-ID:To:From:Subject:Content-Type:List-Unsubscribe:Date;
bh=IReTMq2p4Y99Y1lFEln+pSvcofA=;b=dEWvsIdSK0j5Gmp9ATUlhfDRHQqUR7BolSaqyBh+CzC5WU4iGnn6aBZFtLSi0b4ze+V5nwG3fCAyn4mkAGhdgA7DvJTikspVnn+Jqpu68ru6UnH10WVD8oCJ6aa4Pa6A/sA4Zm52K9h2R7cGQjMOcEZ+N5NNQ6BG9Dtvi+ezKgk=
Received: by trans226.mailxy.com id he8oo0229vgh; Sun, 8 Jan 2017 18:03:04 +0530 (envelope-from <0-22228-gmail.com@delivery.seasonsms.com>)
Delivered-To: someguy@gmail.com
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=pepipost; d=delivery.seasonsms.com;h=Message-ID:To:From:Subject:Content-Type:List-Unsubscribe:Date;bh=ChnX1bsU13QtrayAVkclQsY4c0s=;b=Ziuit9vOzeeAanLi0/
idQ3hTE/Jb3cWs2pMLW71gzQ1/AHgpWYBhXDZoxU8wAmluG/8q2BmnQNKYr9W+ZU1DD4aZHUS1ViqMWYcAdudle3pBb40kLPyk6uCuixu3hXcV/J2d13xEOJ5QkVyiYWYYL1WLxRSOypYBU/7eHWxntiE=
Message-ID: <bmi1.t100.c284046070.1483878782@delivery.seasonsms.com>
To: someguy@gmail.com
From: "Confirmation - Thrifty-Deals" <ezines@delivery.seasonsms.com>
Subject: Confirm your newsletter subscription
Content-Type: text/plain
List-Unsubscribe: <mailto:unsub-aeaaaaaacdxdf5qykzk2kqaivun2lcnkeegsmkob35aq@delivery.seasonsms.com>
X-InjTime: 1483878784
X-Abuse-Reports-To: abuse@pepipost.com
X-FNCID: 22228-14838138016706353-0
X-TransMail: 1
Date: Sun, 8 Jan 2017 18:03:04 +0530
We have received your request to receive the Thrifty-Deals newsletter. Please click below now to complete the process:
http://seasonsms.com/lt.pl?jfklowerwksdfha
Thank you!
Publisher:
Season Publishing House
Newport News, VA 23606
The complete email header would provide much more information on the origin of a message and is a useful tool for tracking and stopping SPAM and virus-laden email.
Whenever you open an email to read, you’ll also find options like View Source, View Message Header or Show Original.
Understanding the different elements of email headers
Received
The header lines begin with Received: and provides a trace of the email from its origin to your mail server. It will show the origin along with the list of servers which processed this email before reaching your mailbox. The ‘Received:’ parameter of your email gives you many valuable clues to identify the legitimacy of the source.
How to analyse the Received parameter in the mail headers
Each mail server which handles an email message adds a Received: header set to the front of the message; the first set is therefore added by your mail server.
The first Received header shows that the email was actually originated from a server with IP address 10.200.41.121
Received: by 10.200.41.121 with SMTP id z54csp461727qtz;
Sun, 8 Jan 2017 04:33:03 -0800 (PST)
In the above example, the header shows the email is actually received From: “Confirmation — Thrifty-Deals” <ezines@seasonsms.com> but the Received: parameter is showing from trans.pepitrans01.com. [103.52.181.228].
Received: from trans.pepitrans01.com (trans.pepitrans01.com. [103.52.181.228])
by mx.google.com with ESMTPS id 94si44473076qtb.140.2017.01.08.04.33.03
for <someguy@gmail.com>
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Sun, 08 Jan 2017 04:33:03 -0800 (PST)
Now, this seems suspicious. Unless trans.pepitrans01.com belongs to the same owner who owns seasonsms.com or the owner of seasonsms.com has given rights to trans.pepitrans01.com to send emails on their behalf.
Let’s check the SPF record of seasonsms.com. This you can easily do on mxtoolbox.com or simply type ~ dig TXT seasonsms.com on your terminal.
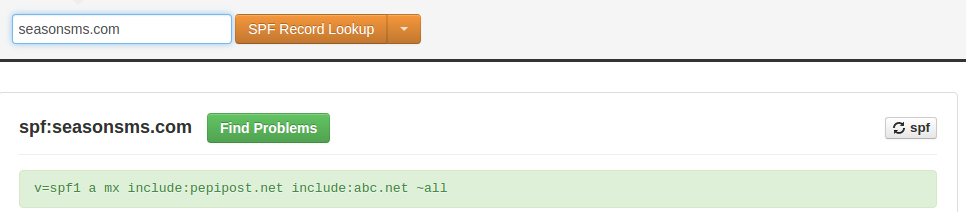
As per the SPF record, seasonsms.com has granted rights to pepipost.net for sending emails on their behalf.
So, now let’s try to valid the actual sending IP address trans.pepitrans01.com. [103.52.181.228] belongs to pepipost.net or not. If that validates, then we are safe to say that email is not spam.
So, let’s check the SPF record of pepipost.net
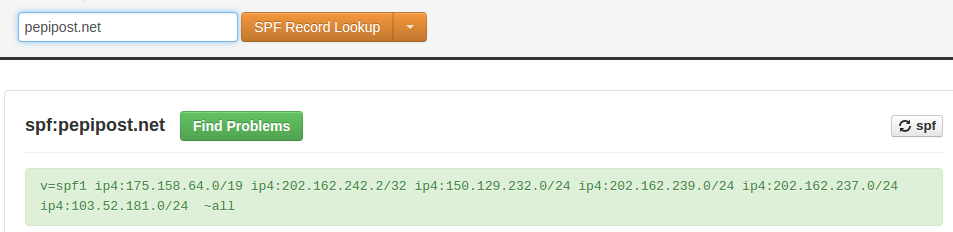
Also, the SPF of trans.pepitrans01.com
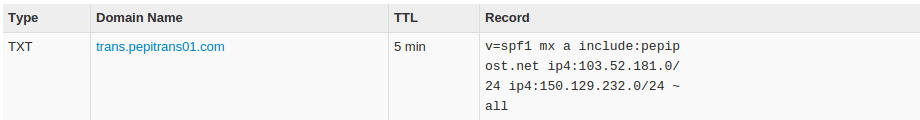
Cool, in both of the above we got same reference of IP address, which is 103.52.181.x here. So, this shows that pepipost.net has allowed 102.52.181.x to send emails on their behalf.
So, the conclusion of this analysis is that
- the user someguy@gmail.com has received an email from ezines@delivery.seasonsms.com via 103.52.181.x IP address which is owned by pepipost.net
- seasonsms’s SPF shows that they have allowed pepipost.net to send emails on their behalf.
Hence, this is a legitimate email and not a forged one.
Received-SPF and DKIM-Signature
In the above example there are two more important parameters, Received-SPF and DKIM-Signature. Not every sender adds these, but most of the good/ big senders have now made it a practice to add SPF and DKIM. These parameters help in identifying the authenticity of the email.
The header parameter in Received-SPF is showing as pass. This means the domain seasonsms.com has allowed the IP address 103.52.181.228 to send emails on their behalf.
This conforms to the analysis which we did earlier.
Received-SPF: pass (google.com: domain of 0-22228-gmail.com@delivery.seasonsms.com designates 103.52.181.228 as permitted sender) client-ip=103.52.181.228;
The next header parameter Authentication-Results: is showing dkim=pass. This means the long public key mentioned in the parameter DKIM-Signature: matches with its associated private key stored on the actual sending server 103.52.181.228/pepipost.net server.
Authentication-Results: mx.google.com;
dkim=pass header.i=@delivery.seasonsms.com;
spf=pass (google.com: domain of 0-22228-gmail.com@delivery.seasonsms.com designates 103.52.181.228 as permitted sender) smtp.mailfrom=0-22228-gmail.com@delivery.seasonsms.com
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=pepipost; d=delivery.seasonsms.com;
h=Message-ID:To:From:Subject:Content-Type:List-Unsubscribe:Date;
bh=IReTMq2p4Y99Y1lFEln+pSvcofA=;b=dEWvsIdSK0j5Gmp9ATUlhfDRHQqUR7BolSaqyBh+CzC5WU4iGnn6aBZFtLSi0b4ze+V5nwG3fCAyn4mkAGhdgA7DvJTikspVnn+Jqpu68ru6UnH10WVD8oCJ6aa4Pa6A/sA4Zm52K9h2R7cGQjMOcEZ+N5NNQ6BG9Dtvi+ezKgk=Received-SPF: pass (google.com: domain of 0-22228-gmail.com@delivery.seasonsms.com designates 103.52.181.228 as permitted sender) client-ip=103.52.181.228;
In the above case the email was sent using a third party SMTP service Pepipost. But, in case the email was sent using their own in-house infrastructure, then the owner of the sender domain and sending IP address should be ideally same (unless on a shared infrastructure).
A number of tools are available for verifying the ownership of a domain/IP address. The authoritative reference for IP addresses is the American Registry of Internet Numbers. Using ARIN’s “Search WHOIS” tool, you can find the identification of the IP address owner.
If nothing works out and you still doubt on the legitimacy of an email then simply send a message to “abuse@organization” with a copy of complete email header (Here is the above example: it will be abuse@seasonsms.com). Most of the webmasters validate and reply to queries received on abuse.
List-Unsubscribe
This is another important parameters parameter in the email header.
List-Unsubscribe:<mailto:unsub-aeaaaaaacdxdf5qykzk2kqaivun2lcnkeegsmkob35aq@delivery.seasonsms.com>
In case the user wants to unsubscribe from an email then simply send an email to this long email address, and user will get unsubscribed.
The List-Unsubscribe header is an optional piece of text. It works in conjunction with options that the email client provides for unsubscribing and spam complaints.
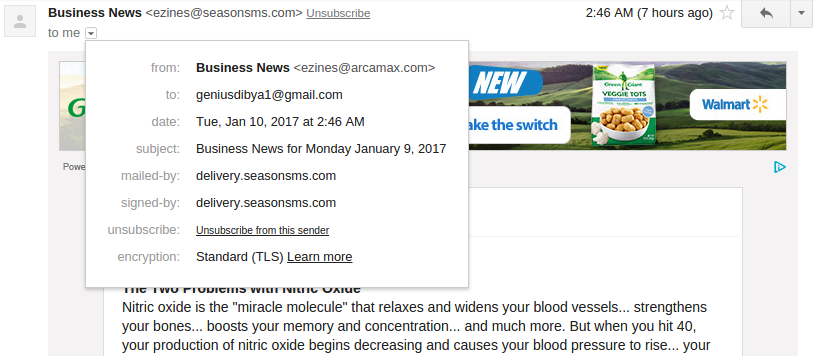
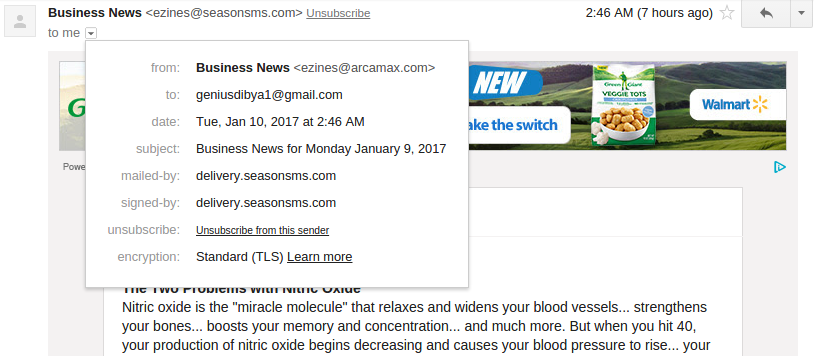
Example: In case of Gmail you will see an option to unsubscribe from this sender. When a user clicks on this link, the email client sends an email to the email address defined in the List-Unsubscribe header parameter.
All email headers prefixed with “X-” are actually not the standard headers. It is added by the sending server for some of their internal tracking and reporting purpose. Hence, these can be simply ignored for any analysis. Example of these headers in the above example are: X-Abuse-Reports-To, X-InjTime, X-FNCID, X-TransMail, X-SG-EID.
Historically, designers and implementers of application protocols have often distinguished between standardized and unstandardized parameters by prefixing the names of unstandardized parameters with the string “X-” or similar constructs. In practice, that convention causes more problems than it solves. Hence it is later depreciated by the IETF community.
Conclusion
We take spam seriously. We are working hard to rebuild and reconstruct the email ecosystem. Let’s together make it spam free. Start analysing your emails and mark unwanted suspicious emails as Spam and stay safe from Phishing.








